Resources
Understanding Role Delegations in Oracle ERP/HCM Cloud
Fraud and Data Loss - one and the same?
Securing the Financial Close
The post GDPR/CCPA world requires you to have complete control over your sensitive data. The problem is gaining visibility over all the Data you have, where it is stored and then implementing effective policies around it. On top of that is the requirement to understand who has access to your Data and their ability to create and update it.
Developers often copy tables or simply create new ones and utilize PII or Sensitive Data when building out new functionality or creating Reports. This increases the footprint of your Data and therefore the Risk of it being compromised.
In addition, if Users have un-filtered access within your Applications, this also creates uncertainty over the management and governance of this Data.

Seecuring has partnered with Mentis to provide a solution that starts with Discovery; Discovery of ALL of your Data assets and Access, and from there, implement the right controls and policies
The Mentis platform enables you to do just that with its integrated suite of modules that helps secure the data across its lifecycle.
Enterprise applications like Oracle E-Business Suite, store large amounts of sensitive data. Mentis enables complete data security at both the application as well as the database layer while removing all exposure to sensitive data.
Uncover hidden sensitive data locations within your enterprise through Mentis’ patented Sensitive Data Discovery module. Find data hidden in all types of data stores in the most obscure locations, be it structured, unstructured, Big Data, or on the Cloud.
Leverage the power of Artificial Intelligence and Natural Language Processing to uncover data in the most complex of locations.
Ensure efficient identification of sensitive data with minimal false positives with a patented approach to data discovery.
Configure any additional data classifications over and above the 70+ out of the box data classifications covering all popular PII and PHI data.
Schedule sample, full, or even incremental scans through a simplified discovery process.
The Seecuring solution enables the discovery of Access issues within your Oracle Applications, encompassing Roles, Responsibilities, Functions and Concurent Programs.
The process:
* Find all Sensitive data, including Custom tables
* Scramble information in lower environments
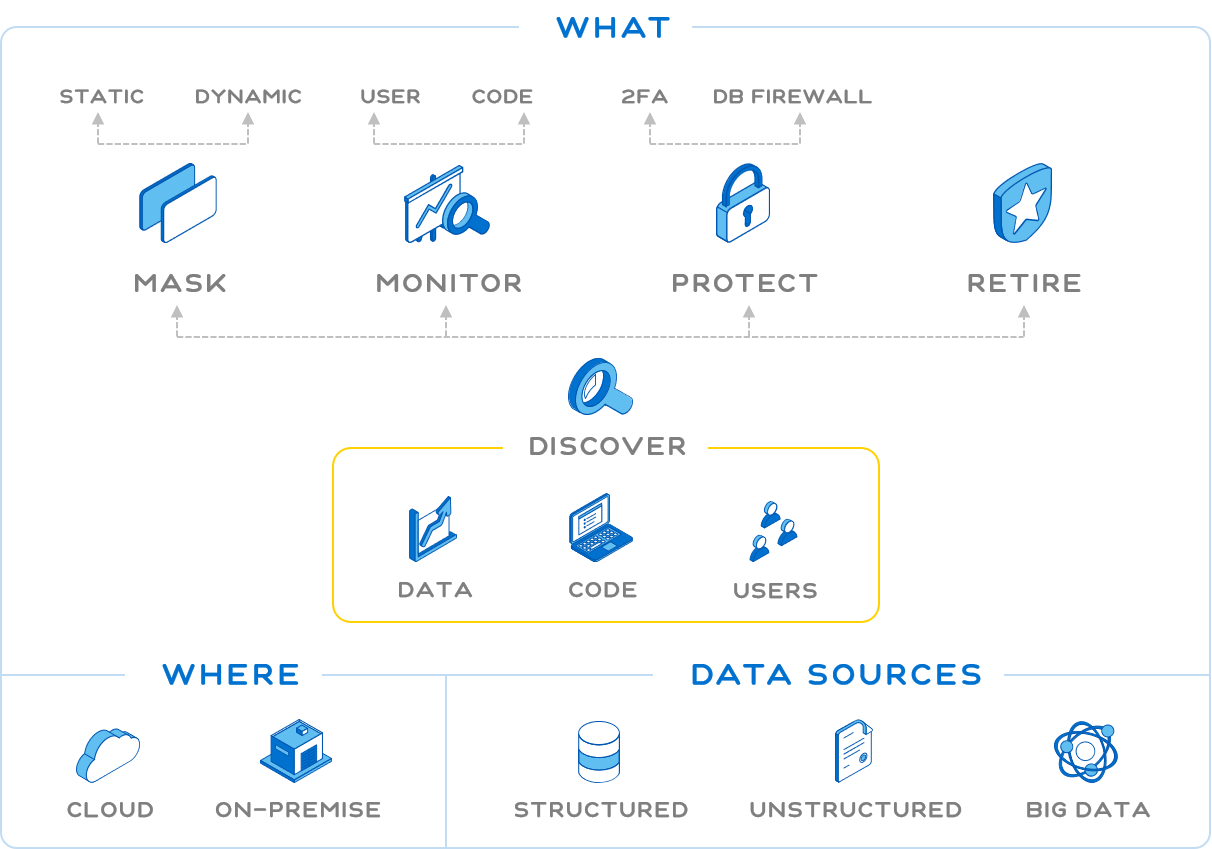
* Mask sensitive data at the database level for unauthorized users
* Mask Application Screens (Forms/ Pages) as well as Reports (PS Queries)
* Enable Right to Know and Right to Erasure compliance regulations
* Analysis of Users, Responsibilities, Functions, Concurrent Programs and more for access to key Data and Transactions
To discuss your Data and Application Security needs you can reach us below:
Fraud and Data Loss - one and the same?
Securing the Financial Close